Introduction
I recently bought a DVID board which is an open source vulnerable designed IoT device. In this post I will try to explain how to solve the second Bluetooth challenge of the DVID project. In this challenge we need to read data from a special characteristic.
Challenge
Let’s flash the firmware, enable Bluetooth and setup the usb dongle:
1 |
|
For this challenge I’ll be using the command line tool bluetoothctl which provide easy commands to interact with Bluetooth devices.
1 |
|
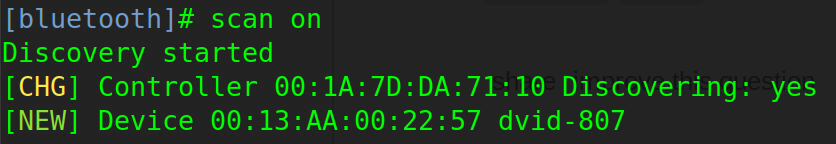
First, you can scan devices which are advertising their presence by using this:
1 |
|
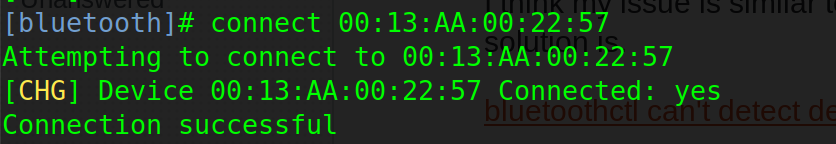
Thanks to the scan we have the MAC address of the Bluetooth device. We can then connect to the device with his MAC address:
1 |
|
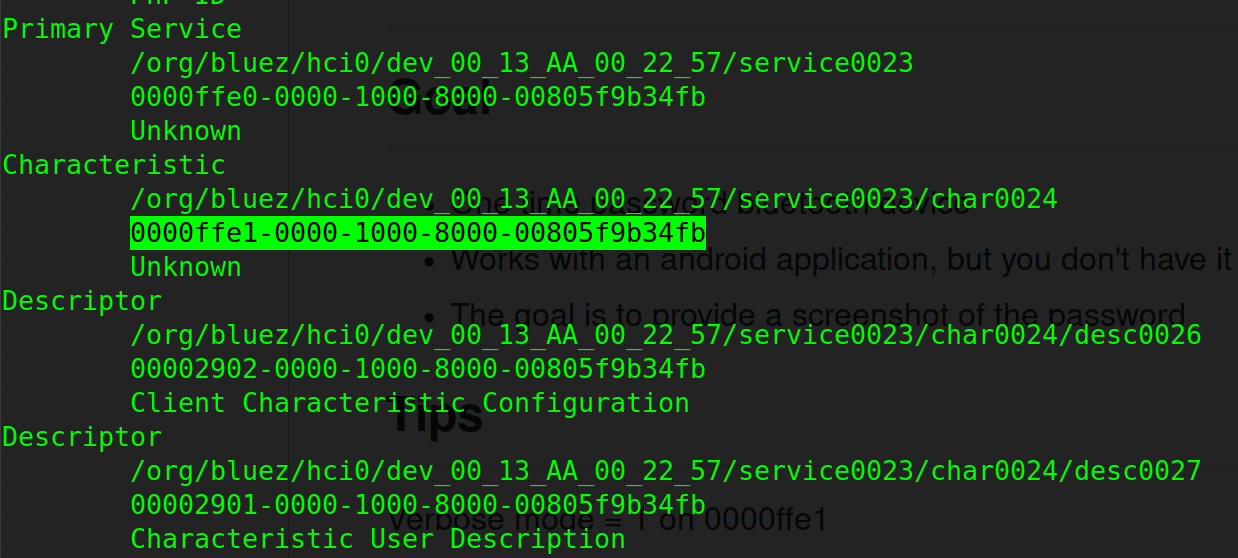
After the connection, to interact with the device you need to use the submenu gatt. Then to get more information about the different services/characteristics you can use this command:
1 |
|
From the challenge tips (Verbose mode = 1 on 0000ffe1) we know that something is leaking on the UUID 0000ffe1.
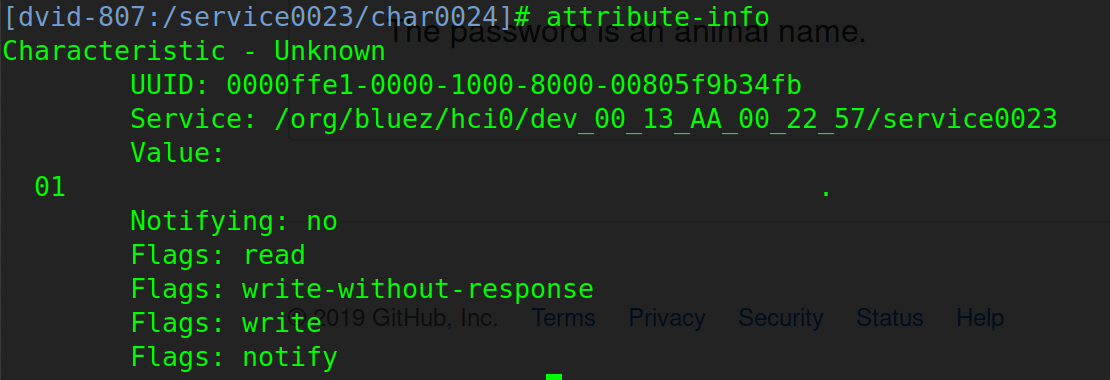
You can select any UUID and get more details with those commands:
1 |
|
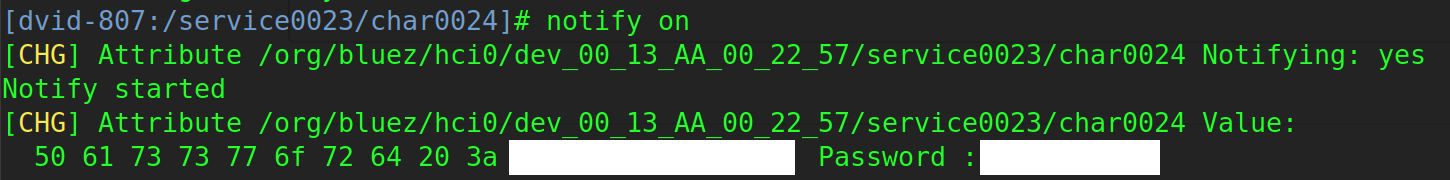
We can see the value 01 but no flag here. Thanks to this command we know which properties can be used with this characteristic. Let’s try to subscribe to notifications. Here is a quick recap of the notify property from my previous post:
The notify property is for receiving periodical update from the Bluetooth device. For example the phone subscribes for a specific characteristic, then the peripheral device sends data asynchronously.
1 |
|
And we get the flag!